Why This Holiday Week Demands Immediate macOS Security Patching
The Attack Window is Open Right Now
Between December 23rd and January 2nd, your organization faces its highest security risk of the year. Security teams are understaffed, response times are measured in days instead of hours, and attackers know it. Recent data shows that 50-61% of all CVE vulnerabilities are exploited within the first 48 hours of disclosure—and this holiday window gives threat actors nearly a week of reduced visibility.
Critical macOS Vulnerabilities Patched This Month
Apple released macOS Tahoe 26.2 and Sequoia 15.7.3 on December 12, 2025, addressing 46 and 25 vulnerabilities respectively. Among these are two WebKit zero-day flaws that Apple confirms were already exploited, “in an extremely sophisticated attack against specific targeted individuals.” On Christmas Day alone, Cisco disclosed CVE-2025-20393, a critical zero-day allowing unauthenticated remote code execution.
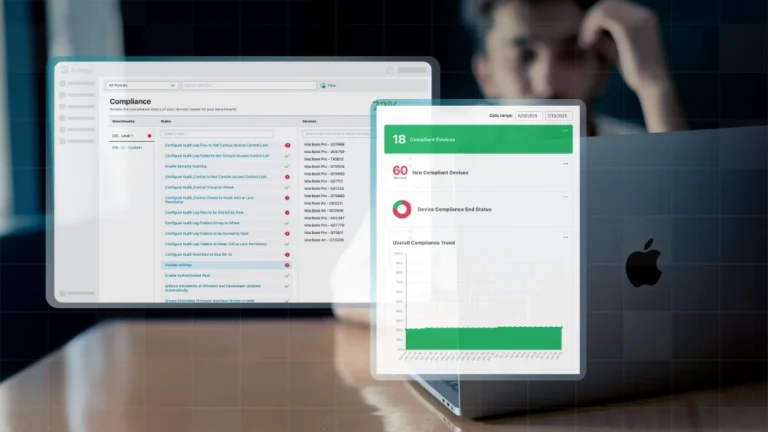
To reduce exposure on Apple fleets, platform teams should lean on an Apple‑first management platform that can enforce OS baselines and automate patch rollout during skeleton‑staff weeks.
Notable macOS CVEs Patched Recently
- CVE-2025-43512: Kernel privilege escalation vulnerability
- CVE-2025-43348: Gatekeeper bypass in Finder and System Settings
- CVE-2025-43412: TCC sandbox escape
- CVE-2025-43373: Wi-Fi kernel memory corruption leading to system termination
With dozens of CVEs landing in a single release, patch management needs to be automated and policy‑driven rather than ticket‑driven and manual.
Why This Week is Your Strategic Advantage
1. Business Continuity Concerns Are Minimal
Major OS updates that typically disrupt workflows have negligible impact during holiday downtime. Push macOS Tahoe 26.2 now while user interruption is at its lowest.
2. Apple’s Support Window is Narrower Than You Think
Apple provides security updates for the three most recent releases—not just two. With macOS Tahoe launched in Fall 2025, Sequoia has limited remaining support life. Organizations still on Sonoma or earlier are already operating outside best practices.
3. The Next Critical Patch is Imminent
Apple typically releases updates every 4-6 weeks. With 26.2 released December 12, expect 26.3 in mid-to-late January. Deploy current patches now so your infrastructure is ready for rapid deployment when 26.3 drops.
Action Plan for Platform Engineers and CISOs
Risk Context: Cybercriminals registered over 18,000 malicious holiday-themed domains this season, with 1.57 million stolen e-commerce credentials circulating on dark web markets. Active exploitation of e-commerce platforms through CVEs like Adobe/Magento CVE-2025-54236 demonstrates attackers are capitalizing on reduced monitoring during this period.
Before January 2nd:
- Deploy macOS Tahoe 26.2 or Sequoia 15.7.3 minimum to all endpoints
- Implement Declarative Device Management (DDM) for automated, policy-driven updates that reduce administrative overhead.
- Enable Rapid Security Response (RSR) auto-install on all devices—these out-of-band patches address zero-days between major releases
- Audit devices still running Sonoma 14.x or earlier and prioritize migration
The Bottom Line
Patching during organizational downtime isn’t optional—it’s your most effective security control when threat actors are most active and your response capability is most limited. The vulnerabilities disclosed this month include kernel-level exploits and Gatekeeper bypasses that undermine your entire security posture.
Deploy updates now, not when you return to a potential breach investigation in January.