Automated Device Enrollment (ADE)
Set up new Apple devices in minutes
Each new machine added to your environment needs to have certain company software, security and network settings—they need to be managed right out of the box. ADE and Addigy solve that easily.
Zero-Touch Deployment for Maximum Productivity
Up and Running and Hassle-Free
Configure and deploy devices quickly, securely, and efficiently. Employees receive a fully managed device straight out of the box—ready for work in mere minutes. Say goodbye to time-consuming manual setups. Addigy’s Automated Device Enrollment (ADE) takes the complexity out of Mac management.
Right out of the box
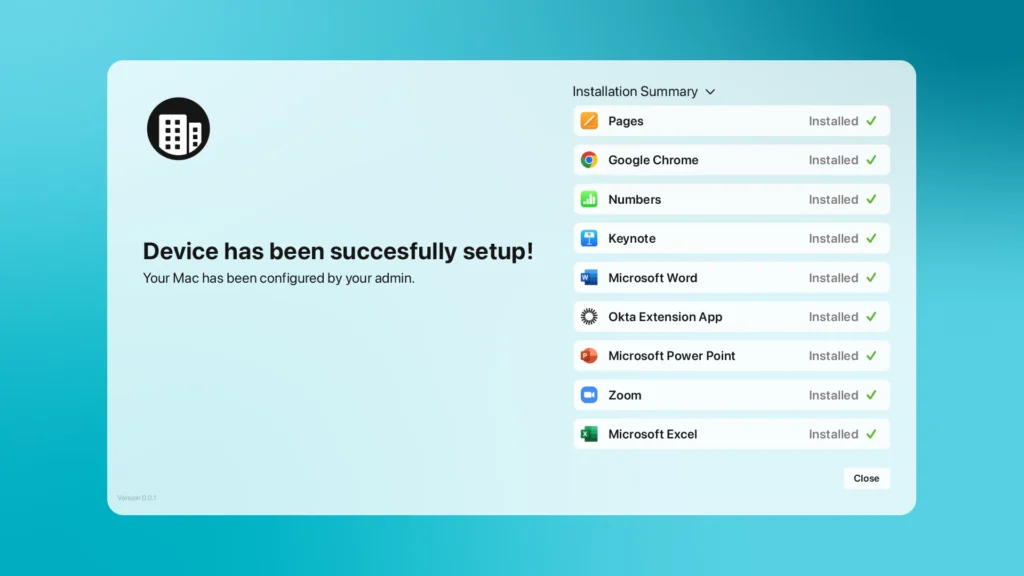
Devices are pre-configured with your company’s software, security settings, network access, and compliance requirements—all during the device’s Setup Assistant process.
Role-Specific Configuration
Automatically deploy the right apps and settings tailored to an employee’s role, so the tools they need are ready to go from Day One.
Single Sign-On Integration
During device setup, employees log in with Google, Okta, Azure, or any SAML provider. Simple for them, secure for you.
Simplify and Customize Mac Setups
Boost efficiency and reduce frustration with Addigy Assist. Designed with IT teams and Managed Service Providers (MSPs) in mind, Addigy Assist transforms setup processes into a streamlined, elegant experience.
Apple-Native UI
A sleek, modern user interface that feels intuitive and familiar for end users
Real-Time Progress Updates
Keep users informed as their devices update and configure in real-time, reducing uncertainty and confusion
Automated Workflows
Save time with automated software installations and network setups, ensuring devices are work-ready faster
Custom Branding
Personalize Setup Assistant flows with your organization’s logo, unique authentication codes, and required Terms of Service or Privacy Policy pages
Smart Prompts
Handle interruptions like low battery, network issues, or user-initiated restarts to ensure a flawless setup process
Immediate Visibility
Newly configured devices automatically appear in Addigy, providing IT admins with instant oversight and control
Multi-Tenant Scalability
Create tailored configurations for different teams or clients while maintaining centralized oversight
Most onboarding solutions are either too complex or too rigid, requiring hours of setup, maintenance, and troubleshooting. Meanwhile, end users are left frustrated, confused, and constantly reaching out to IT for help. With Addigy Assist, I had it fully deployed in under 10 minutes, giving employees a smooth, transparent setup experience from day one. Less time wasted, fewer tickets, and a better first impression for new hires.
Why admins choose Addigy to manage their Apple fleet
Secure & Scalable
From small teams to enterprise-level businesses, Addigy’s flexible and secure solutions grow with your organization’s needs.
Time-Saving Automation
Eliminate hours of manual setup with workflows that configure devices in minutes.
End-User Experience
Employees experience a smooth onboarding process that minimizes frustration and maximizes productivity from the get-go.
Effortless Device Management Starts Here
Drive productivity, save time, and streamline onboarding with Addigy’s powerful Automated Device Enrollment solution. Whether you’re onboarding a new hire or refreshing devices for an entire team, Addigy ensures every Mac is always setup perfectly.