How To Run a Script To Bypass Security Bug for macOS (versions 10.15 to 11.2)
A serious security bug, with the identifier CVE-2021-30657, has recently been publicized and patched. However, it has been used in the wild since early January and affects devices with macOS version 10.15 to 11.2 but has been patched as of 11.3. This bug essentially allows a downloaded application bundle to bypass all of Apple’s security mechanisms (File Quarantine, Gatekeeper, Application Notarization) and execute an arbitrary script.
Apply the following updates to your Policies to update macOS 10.15 and macOS 11 to patch the vulnerability:
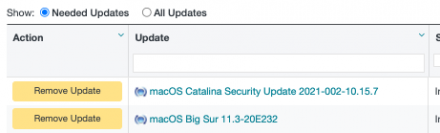
- macOS Catalina Security Update 2021-002-10.15.7
- macOS Big Sur 11.3-20E232
Before the discovery of this bug, any attempt to launch an application downloaded from the internet would have to go through three different security features of macOS:
- File Quarantine – implemented in 10.5 which alerts the user that they’re attempting to run an application.
- Gatekeeper – implemented in 10.7 which blocks applications from unidentified developers. Though it was trivial for malware developers to acquire Apple Developer IDs to sign their malware.
- Application Notarization – implemented in 10.15 which is Apple’s automated system that scans for malicious content and approves software before it is allowed to run.
However, there is a way to run a script that bypasses these prompts and security checks while masking it as an innocuous file such as a PDF or DMG. This can be done trivially by putting a bash script in the directory structure of a bare-bones application bundle with no Info.plist file. Any script without an Info.plist is not recognized as an application and will execute without any security checks or prompts.
The structure follows like this (where “application” is the bash script payload):
- application.app/Contents
- application.app/Contents/MacOS
- application.app/Contents/MacOS/application
The script needs to have the same name as the application bundle for it to work.
This application is then distributed as either a PDF, DMG, etc, and when double-clicked, it is executed instantaneously while bypassing security checks. In fact, the bug is currently being used in the wild by the Shlayer malware which is an adware that injects ads into web pages.
The bug has been patched as of macOS 11.3 so updating will prevent it from being exploited on your machine. For those running older versions of macOS, BlockBlock with “Notarization Mode” enabled protects against this.
Mac security researcher Patrick Wardle published an extensively detailed report regarding the bug on his blog which also contains a proof of concept. Furthermore, he has provided a python script that detects past exploitation attempts.