Randomized MAC Addresses: What IT Admins Need to Know
As Apple devices continue to evolve with privacy-focused features, one advancement that has been introduced for IT environments to work with is MAC address randomization. Originally introduced to shield users from location tracking, the feature may play a role in network headaches for IT teams trying to maintain secure but also consistent access to corporate networks.
MAC randomization was designed with good intentions. By rotating a device’s network identity, it limits passive tracking by third-party observers. However, in enterprise environments where reliability, security, and predictability matter this shift can severely hinder core IT operations. If devices can’t be reliably identified, things like authentication, auditing, and automated policy enforcement begin to fall apart.
So, what is a randomized MAC address? More importantly, how can IT admins mitigate the chaos it can introduce in enterprise network environments? This post takes you through the fundamentals, challenges, and management strategies that every IT team should know.
What Is a MAC Address?
A MAC (Media Access Control) address is a unique identifier assigned to a device’s network interface controller (NIC). It is how devices communicate within a local network, functioning like a digital address that distinguishes one device from another.
MAC addresses operate at Layer 2 of the OSI model and are crucial for facilitating local communications over Wi-Fi and Ethernet. Routers and switches use them to route data packets to the correct destination. The addresses are typically hard-coded into hardware by manufacturers and follow a consistent format, like 00:1B:44:11:3A:B7.
Because MAC addresses are often static, they become reliable identifiers. IT administrators use them for tasks like IP address reservations, device-specific firewall rules, and access permissions. In essence, MAC addresses are a pillar of network-based identity and access control.
What Is a Randomized MAC Address?
A randomized MAC address protects user privacy by creating a temporary, software-generated identifier for each WiFi network that masks your device’s actual hardware address. Apple first introduced this feature with iOS 14 as a new “Wi-Fi privacy feature”, and it became the default behavior for all Wi-Fi connections.
The purpose of MAC randomization is to protect user privacy by preventing third parties from tracking devices across different Wi-Fi networks. In public spaces malicious actors could use static identifiers to monitor a user’s movement, behavior, and habits. Randomization interrupts this tracking by changing the device’s visible address.
Why a Randomized MAC Address Matters
While this shift is a win for end user privacy, it creates friction in enterprise settings where consistency is paramount. For IT teams, randomized MAC addresses may obscure device identity, making it difficult to enforce policies, monitor activity, and ensure secure access.
For example, a device that was approved on the network yesterday may show up as entirely new today, leading to failed authentications or duplicated entries in management network systems. As a result, what protects individuals in public environments can cause major disruptions in managed, secure enterprise networks.
How do I Identify a Randomized MAC Address?
Randomized MACs aren’t entirely opaque—IT admins can still identify them using structural clues. One way is by examining the second hexadecimal digit of the MAC address. If this digit is 2, 6, A (or a), or E (or e), the address is locally administered and likely randomized.
Common Formats:
- x2:xx:xx:xx:xx:xx
- x6:xx:xx:xx:xx:xx
- xA:xx:xx:xx:xx:xx
- xE:xx:xx:xx:xx:xx
In addition to manual inspection, device settings offer further clues. On Apple devices:
- iOS & iPadOS: Go to Settings > Wi-Fi > [network name] > Information icon. Look for the “Private Wi-Fi Address” toggle.
- macOS: Open System Settings > Wi-Fi > [network name] > Details… and check for the “Private Wi-Fi Address” status.
Admins can use these indicators to determine whether a device is using its real MAC or a randomized one, and adjust their policies accordingly.
How does MAC Randomization Affect Secure Wi-Fi?
While MAC randomization benefits users in public spaces, it can disrupt the operation of enterprise Wi-Fi environments that rely on stable device identities. The consequences manifest in several critical areas of IT infrastructure:
Authentication Workflows
Many enterprise networks use MAC-based authentication to allow or deny access. These systems rely on recognizing a device’s MAC as an identifier. When a MAC address changes unexpectedly, the network can no longer associate the device with previous sessions or policies, often resulting in failed logins.
This inconsistency creates an unreliable user experience. Employees may find that a device that connected yesterday no longer works today, leading to confusion, productivity loss, and increased support requests.
Security Event Logging
In enterprise environments, tracking who did what and when is vital. Firewalls, intrusion detection systems, and SIEM platforms log events based on MAC addresses. When those addresses rotate, tracing a device’s activity becomes nearly impossible.
Security teams may struggle to correlate suspicious activity across sessions, undermining their ability to detect, investigate, and respond to threats effectively. Repeat offenders can appear as new users, and policy violations may go unnoticed.
Device Tracking Tools
Organizations that use device location tracking for purposes like foot traffic analysis, space utilization, or employee safety will also see reduced accuracy. A single user’s phone may appear as several different devices throughout the day, making analytics unreliable and potentially invalidating data-driven decisions.
Randomized MAC Address Friction: “Sticky Clients” & Duplicate Devices
One of the most common pain points IT teams face is the “sticky client” problem. This occurs when a device loses connection and reauthenticates with a new MAC address. Because the network sees it as a brand-new device, it prompts for credentials or fails to auto-join altogether.
This issue leads to a surge in helpdesk tickets, confused users, and wasted IT resources. Monitoring tools may also display multiple instances of the same device, skewing data and complicating device management.
The impact isn’t just technical; it undermines the user experience and puts IT in a constant reactive state.
Network Services at Risk: What Breaks with MAC Randomization?
Randomization disrupts several key network services that depend on stable MAC addresses. Here are a few examples:
| Network Service | What Breaks |
| DHCP Reservations | IPs can no longer be reliably assigned to a specific device |
| Network Access Control (NAC) | MAC-based rules fail to enforce intended access policies |
| Captive Portals | Session tracking fails, leading to login issues or repeated prompts |
| Wi-Fi Analytics | Data becomes fragmented, reducing the effectiveness of network insights |
Without centralized control, these issues compound quickly. Even tech-savvy users may not realize their device is rotating MACs, leaving IT teams to deal with invisible and unpredictable behavior.
Can Users Turn Off MAC Address Randomization?
Yes. Apple allows users to disable MAC randomization per network. However, the default behavior is for the feature to be turned on, and users often don’t realize it’s enabled. This can result in recurring issues every time they connect to secure or managed Wi-Fi.
How to Disable MAC Randomization
- iOS & iPadOS 14 and later:
- Navigate to Settings > Wi-Fi
- Tap the info (i) icon next to the network name
- Toggle Private Wi-Fi Address to OFF
- macOS 15 and later:
- Go to System Settings > Wi-Fi
- Tap Details… next to the connected network
- Toggle Private Wi-Fi Address to OFF
Note: If the user resets network settings, wipes the device, or sets it up as new, MAC randomization will be re-enabled by default. The only exception is during Setup Assistant, where the hardware MAC is used initially.
Managing MAC Address Randomization with MDM
In managed environments, the most effective way to deal with MAC randomization is by using a Mobile Device Management (MDM) solution. This allows IT admins to configure and enforce network behavior at scale across all Apple devices.
What You Can Do with MDM
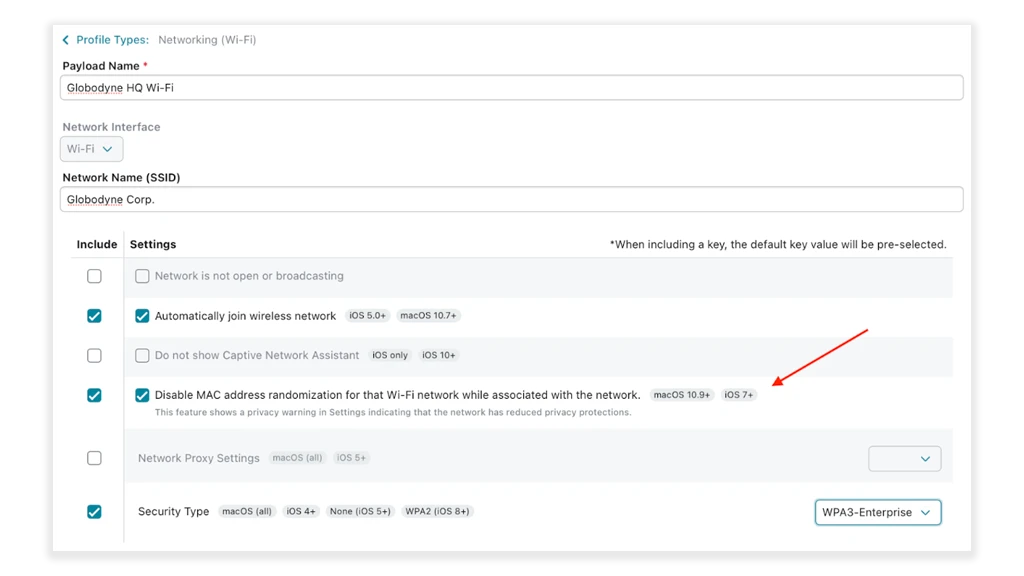
- Push Wi-Fi profiles that disable MAC randomization for specific SSIDs
- Starting with macOS 15.4+ when Private Wi-Fi Address is disabled by the MDM managed profile for a managed Wi-Fi network, it cannot be manually enabled for that network by the user.
Source: https://support.apple.com/en-us/121011 - This option can be found in the Addigy MDM Profile Catalog under the Wi-Fi payload:
- Starting with macOS 15.4+ when Private Wi-Fi Address is disabled by the MDM managed profile for a managed Wi-Fi network, it cannot be manually enabled for that network by the user.
- Enforce trusted network rules to use hardware MACs only
- Monitor compliance to ensure users aren’t bypassing settings
- Reduce helpdesk load by automating consistent behavior across all devices
The Addigy Apple MDM Advantage
Addigy makes all of this seamless. With real-time device monitoring and automation, Addigy helps IT teams identify and address connectivity issues before they become widespread. From syncing credentials with Addigy Identity to enforcing policy-based MAC behavior via MDM Profile, Addigy gives IT the tools to maintain reliable, secure device access across all Apple hardware.
Admins can centrally configure Wi-Fi profiles, monitor randomized MAC usage, and ensure every device meets compliance standards—even as Apple devices evolve.
Final Thoughts on Randomized Mac Addresses
Randomized MAC addresses were created to enhance personal privacy, but they come at a cost for enterprise IT. From authentication failures to inaccurate analytics, the consequences are far-reaching when MAC randomization isn’t managed properly.
With the right MDM platform, like Addigy, IT teams can take control. Whether you’re disabling randomization on trusted networks or ensuring compliance across thousands of devices, Addigy delivers the automation, visibility, and flexibility needed to make Apple device management frictionless.
Need help configuring MAC behavior across your Apple fleet?
See how Addigy simplifies secure Wi-Fi access and MDM configuration







