How to Create Multiple Layers of Security to Build a Secure Environment
Security is important for all devices and macOS environments are no exception. More and more we are seeing reports of new attacks and malware that specifically target macOS such as XLoader, Silver Sparrow, Shlayer, and XCSSET, just to name a few. So knowing how to secure your environment should be a priority.
We already have an article covering the many ways you can configure macOS to harden your device. In honor of Cybersecurity Awareness Month, we’ve compiled a list of additional steps you can take today to improve your security posture.
Log Collection and Analysis
Collecting and analyzing logs will give you insight into everything that goes on in your network and macOS devices.
Consider using a Security Information and Event Management (SIEM) tool to consolidate your logs for analysis. A SIEM can provide dashboards and alerts for correlated events. In addition, they can be used to create custom rules to stop all kinds of attacks by detecting anomalous activity.
This is especially useful for compliance and auditing purposes as it gives auditors a view into your logging and monitoring capabilities.
Application Blacklisting/Whitelisting
For really granular control over what applications should be allowed or disallowed on a macOS system, we recommend using Google’s binary authorization system Santa. Check out how to use Santa with Addigy.
Santa monitors for binary executions and determines whether to allow or block them based on a database residing on the device, it also provides a “lockdown” mode for another level of granular control on devices. Optionally, you can provision a server that Santa syncs to for multiple devices to retrieve rules from.

Host-based Intrusion Detection System
A host-based intrusion detection system (HIDS) resides on the endpoint system and monitors the entire system and network traffic for any malicious activity or anomalous behavior.
One HIDS that we recommend is OSSEC which is a free and open-source solution.
Some of its capabilities include log analysis, file integrity monitoring, rootkit detection, real-time alerting, and active response. Its components consist of an agent and a server (if you’re operating on multiple devices).
Backup
With the increasing threat of ransomware and potential data loss, having a proper backup solution set up is paramount. Without backups, you run the risk of permanent data loss in the case of an attack or catastrophic failure.
What and how you backup is entirely dependent on your business needs. However, you would generally want to backup critical data at least daily so that in case of a catastrophe there would only be a day’s worth of data lost. An automated backup solution would simplify this process.
It would be best to go with a cloud backup solution. They are often much more secure than on-premise backups and are very convenient with their automated features.
Process and File Monitoring/Blocking
If malware were to somehow get into any of your macOS systems, it would be good to have another line of defense.
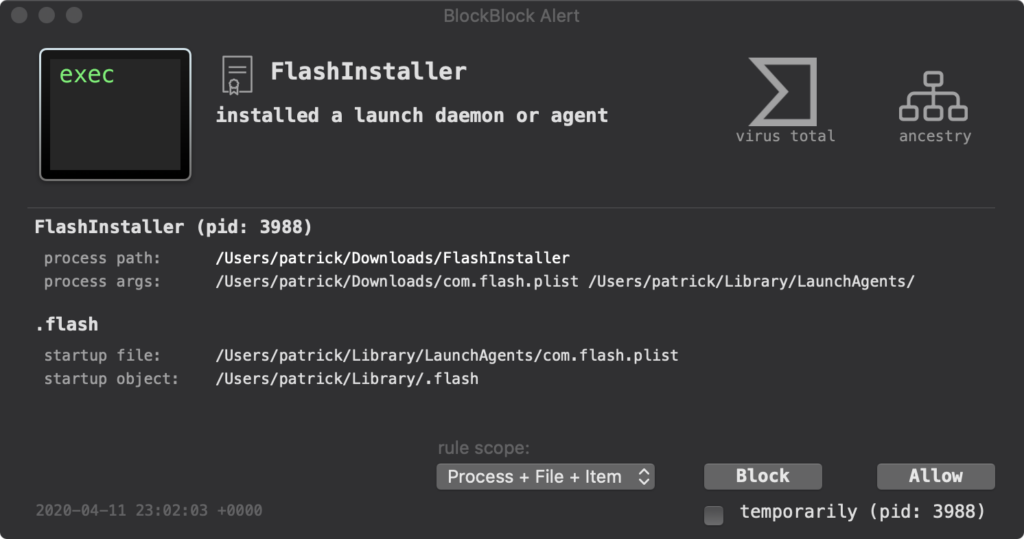
Malware commonly attempts to establish persistence in the form of Launch Daemons and Launch Agents. BlockBlock is one tool that helps fight against this. It monitors for common ways that malware establishes persistence and alerts for any attempts.
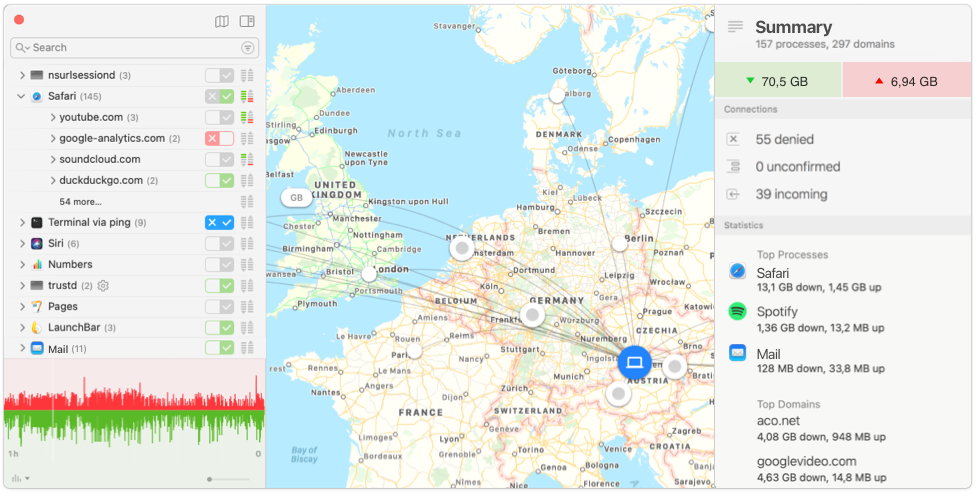
Another useful tool is Little Snitch. It allows you to control connections to the internet made by your applications. It also lets you visualize these connections so that you can see exactly where and what you’re connecting to. Malware typically connects back to a Command and Control server so this would make it easier to find malicious connections.
Ad Blocker
The internet is filled with malicious advertisements to the point where it’s a security concern to not have an ad blocker installed. Some of these kinds of ads don’t require direct interaction from the user, just by loading a webpage they can take advantage of vulnerabilities in your browser with javascript.
Windows is typically the target for these ads but macOS is becoming more of a target as well. An ad blocker would significantly reduce the chances of malicious ads infecting your system with malware.
An ad blocker we recommend is uBlock Origin. In addition to its ad blocking capabilities, it blocks trackers and known malware domains. It uses several filter lists that are constantly being updated.
—
This blog post was written by Nathan Pabon, Application Security Engineer, and Nicolas Ponce, Vice President of Operations and Security.