Mitigating Zoom and RingCentral Zero-Day Vulnerabilities
Vulnerability Overview
On Monday, July 8th, 2019, a Zero-day vulnerability was announced by Security Researcher, Jonathan Leitschuh, that explained how Zoom and RingCentral meetings applications can allow any website to forcibly join a user to a Zoom/RingCentral meeting and activate their video camera, with no end-user approval required.
Read Jonathan’s full writeup on the vulnerability.
Update 7/10/2019: Apple pushes silent and automatic upgrade to macOS devices.
Update 7/9/2019: Zoom has recommended to update to their latest version (4.4.53932.0709) for the latest version that fixes this vulnerability.

How To Protect Your Devices
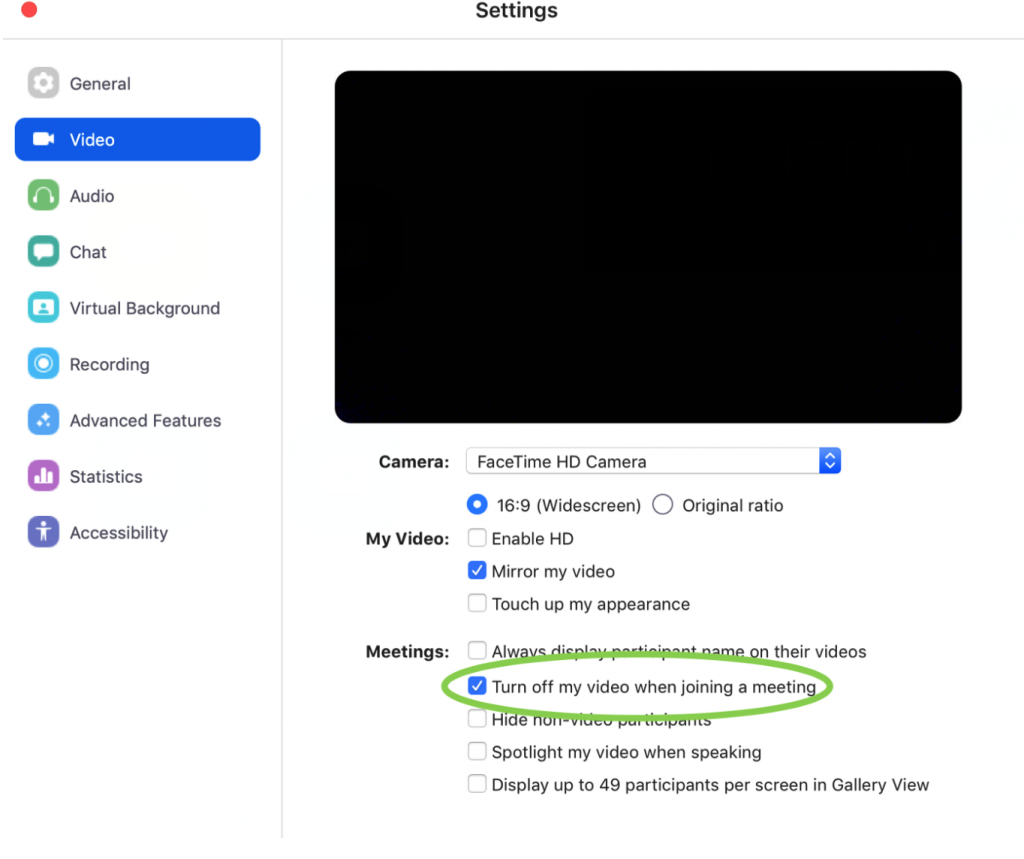
1. Disable your webcam in Zoom/RingCentral meetings and/or use a webcam cover if you don’t have one:
2. Copy the Addigy community script “Patch Zoom vulnerability” and instantly deploy it across your fleet:
P.S. Big thank you to Addigy community member @Shawn Maddock for the script submission!
Now What?
Zoom is a widely-adopted, remote meeting solution used by organizations around the world. Balancing the need for user privacy and security with convenient features, such as shareable remote meeting links, has become highly challenging. Addigy can help you identify and mitigate the risks associated with this vulnerability, as well as many others. Our Custom Scripts and Custom Facts engine allows you to easily collect any device data that can then be used to send alerts and trigger automated remediation.