“AirBorne” Vulnerabilities
Oligo Security Research has recently published multiple security vulnerabilities relating to Apple’s AirPlay Protocol and AirPlay Software Development Kit (SDK).
Some of the most serious vulnerabilities involve zero-click and one-click remote code execution (RCE), access control list (ACL) and user interaction bypass, man-in-the-middle attacks, and denial of service (DoS).
Oligo Security has named these vulnerabilities “AirBorne” since if the attacks are chained together they allow an attacker to take over any Airplay-enabled devices and spread malware to other devices in any network it connects to. This includes devices such as a Mac, iPhone, iPad, AppleTV, and even CarPlay enabled devices.
One of the vulnerabilities, a macOS zero-click RCE with the ID of CVE-2025-24252, allows an attacker to execute arbitrary code on devices connected on the same network that have the AirPlay receiver on with the “Anyone on the same network” or “Everyone” configuration. It does this without prompting the user when chained with CVE-2025-24206 (a user interaction bypass). This can then be used to exploit other devices on the same network and other networks the device is connected to.
CVE-2025-24252 and CVE-2025-24206 has been fixed in the following updates:
- iOS and iPadOS 18.4
- iPad OS 17.7.6
- macOS Sequoia 15.4
- macOS Sonoma 14.7.5
- macOS Ventura 13.7.5
- tvOS 18.4
- visionOS 2.4
Another vulnerability, a zero-click RCE involving the AirPlay SDK (CVE-2025-24132), allows an attacker to execute arbitrary code on speakers and receivers that leverage the AirPlay SDK. These compromised devices could then be used to spread to others without any human interaction and could enable attackers to listen to nearby conversations with the device microphone.
CVE-2025-24132 has been fixed in AirPlay audio SDK 2.7.1, AirPlay video SDK 3.6.0.126, and CarPlay Communication Plug-in R18.1.
Oligo Security recommends the following:
- Update devices to the latest versions using Addigy’s Updates Feature.
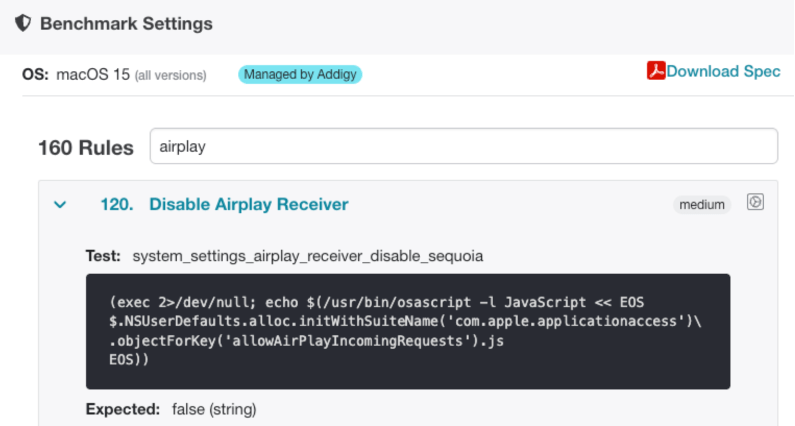
- Disable AirPlay receiver if it is not in use with 1-Click Compliance.
- Restrict AirPlay Access to only trusted devices with firewall rules on port 7000 on your network.
- Restrict AirPlay settings by changing the “Allow AirPlay for” configuration to “Current User” which doesn’t prevent all of the vulnerabilities but does reduce the attack surface.
Addigy can be leveraged to disable the AirPlay receiver with a Profile configuration or with a 1-Click Compliance Benchmark (Both CIS and DISA Benchmarks) deployed to your devices.